Loading times..
Some loading thoughts
Post-quantum cryptography is coming. Sometime soon, it has been said. There are many challenges in that area (some of them that we have outlined over here). There is, however, a big question that still pokes in my head: if post-quantum cryptography may potentially slow our connections, how slow is too slow for end-users?
In order, to answer this question, I first wanted to dig in into how fast websites should load in 2022. My findings seem to be that ‘every second counts’. Let’s see now why.
“Faster is better and less is more”
In 2017, it was reported that “the average time it takes to fully load a mobile landing page is 22 seconds”. Yet, “53% of visits are abandoned if a mobile site takes longer than three seconds to load”. The reasons for this abandonment seem to vary, but it is still poignant to note that users still mainly remain on websites that load on the desktop rather than on mobile devices.
Prior to analyzing why users leave websites, we first need to understand something:
- A ‘slow’ website can be perceived as ‘fast’ by another user due to personal feelings or cultural perceptions.
- A ‘fast’ website can be ‘fast’ for a user, as it is on a fast network with a powerful device. The same ‘fast’ website can be perceived as ‘slow’ by someone on a slow network with a not-so-powerful device.
- A site can be perceived as loading ‘faster’ if content is progressively loaded.
- A site can be perceived as ‘loaded-fast’ but ‘slow’ to user-interaction on it.
“Historically, web performance has been measured with the load event. However,
even though load is a well-defined moment in a page’s lifecycle, that moment
doesn’t necessarily correspond with anything the user cares about.
For example, a server could respond with a minimal page that “loads” immediately but then defers fetching content and displaying anything on the page until several seconds after the load event fires. While such a page might technically have a fast load time, that time would not correspond to how a user actually experiences the page loading.”, as noted here.
Rather that relying on load, there seems to be two main user-centered metrics
to take into account:
- Largest Contentful Paint (LCP): measures perceived load speed as it marks the point in the page load timeline when the page’s main content has likely loaded.
- First Contentful Paint: measures perceived load speed as it marks the first point in the page load timeline when the user sees anything on the screen.
To provide a good user experience, sites should strive to have LCP of 2.5 seconds
or less. This is roughly based on the research of Miller and Card et al:
the amount of time a user will wait before losing focus is a range from roughly 0.3
to 3 seconds. Speed then continues to be a core vital for users to engage on a
website or not. FCP needs to be fast as well (1.8 seconds or less.) as users
need to be reassured that something is happening.
Yet, as reported by Google in 2017, “for 70% of the pages we analyzed, it took nearly seven seconds for the visual content above the fold to display on the screen, and it took more than 10 seconds to fully load all visual content above and below the fold.” They also found that less is definitely better for website loading: “70% of pages were over 1MB, 36% over 2MB and 12% over 4MB. That’s enormous for a single mobile page, given that 1.49MB takes seven seconds to load using a fast 3G connection. One image in particular caught our attention: It weighed a whopping 16MB.”
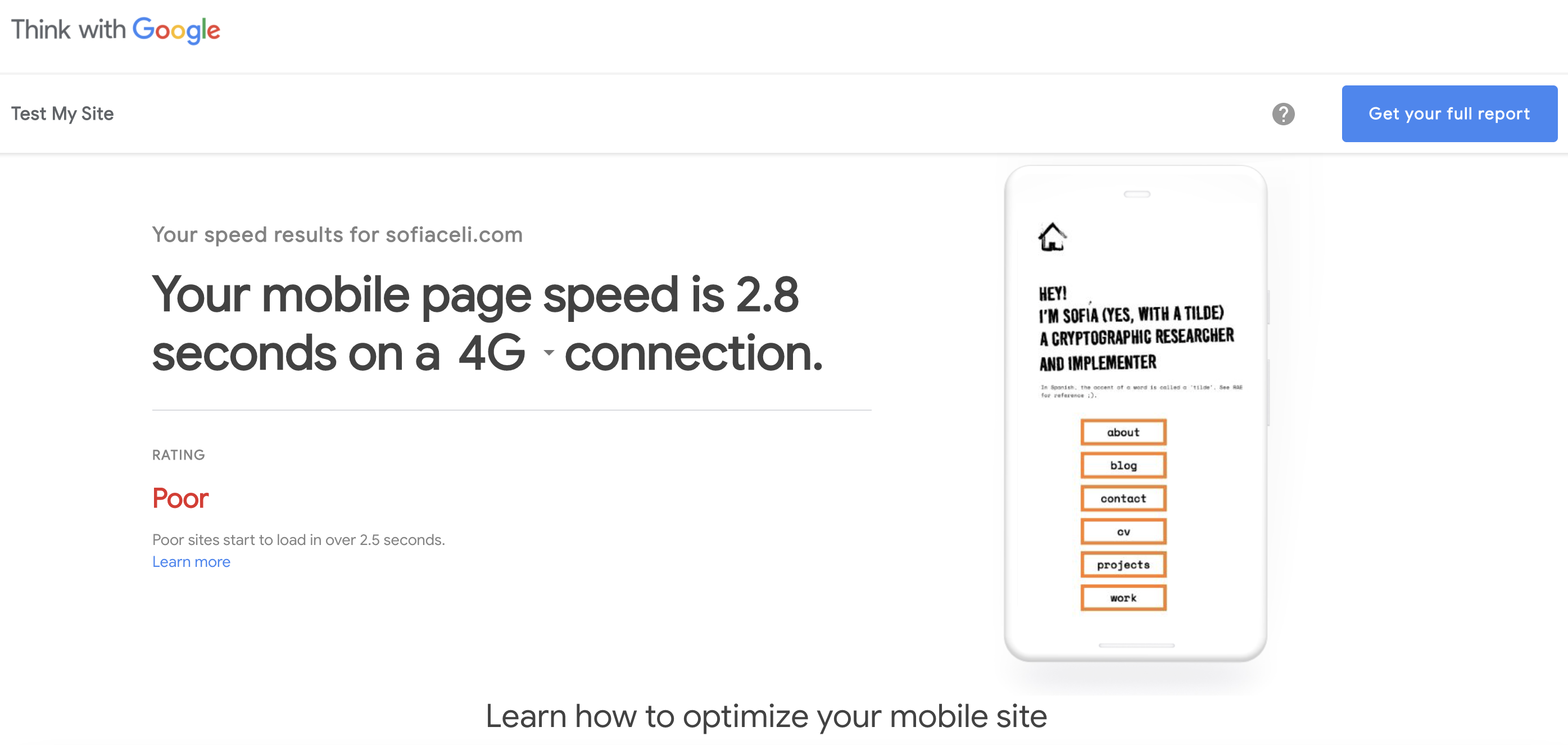
Given these metrics, even my site has bad loading times (as tested here):
Does TLS make websites slow? What about post-quantum?
So, let’s go back to the question. The reason why we need post-quantum cryptography is due to quantum computers arrival and the threat to cryptography they pose. Where are we going to mainly be using post-quantum cryptography? We will need to mainly incorporate it into TLS.
The good new is that today TLS is fast. Usually, the process of communicating over an encrypted channel introduces additional costs due to the increases that asymmetric and symmetric cryptographic operations introduce. Modern hardware, though, has minimized these costs. The usage of resumption mechanisms, such as “zero round trip” (0-RTT), has minimized it as well (for more explanations around the matter, see this article).
Does this mean that the same will happen when we migrate TLS to post-quantum cryptography? Potentially, no. It first depends on the type of post-quantum cryptography that will be used (lattices are faster than isogenies, for example). Second, it depends on if the newly introduced cryptography will cause extra round-trips at the network layer or not. And, third, it still debated how these extra costs will impact the user-centered metrics that we just outlined.
So far, there has not been much research on the impact of post-quantum cryptography on end-users: will users see the web loading times that they have grown accustomed to degrade?, will users care if the loading time is slightly increased?, will it be more visible on the mobile experience?
I’m now seeking to explore more on these questions, as well as the understanding
of metrics that take the user experience into account, as load metrics
seem to not be enough.
